General Report on Tunny
11E Page 15
The exchanges were connected by a further link (DACE) and there were 6 cross country links.
(a) The period of Flux.
From July 1944 - May 1945, the organisation of the Tunny network became increasingly disorganised as German Army units and even German Headquarters stations moved to new positions. Nearly all links had their terminus moved to new exchanges as Zossen near Berlin between July 1944 and October 1944. When Berlin was threatened part of these exchanges moved first to Erfurt then back to Berlin, and ultimately (by the end of the war) to Salzburg. Charts showing the Tunny network at various times in 1944-5 are given in Part 6.
Cipher security was tightened up in the summer of 1944 and by August 1st a daily change of all wheel patterns had been introduced on each link. SZ42B was first used on Codfish in June 1944 and about half the Tunny links were issued with this machine. At first it was used (SZ42A was then used) with the P5 limitation switched in (i.e. on Ψ1 P5 lim) but later it was decided that the P5 attachment on both machines gave more trouble than it was worth, and it dropped out of use from September 1944 onwards.
By May 1945 the German Army was in a state of complete disorganisation and the last Tunny message was sent on 8th May, 1945.
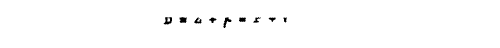
For practical, if not logical, simplicity it will be found that P, K, Ψ', D and Z are sometimes used to refer not to any specific letter in the active position but to the whole of the stream concerned.
Further, now that the distinction between a message and a transmission has been carefully drawn, it will be convenient to refer to each of these as a message. This practice is in accordance with traditional usage and agrees with that found in the Research Logs and other contemporary Tunny documents. The exact meaning will usually be clear from the context.
(b) Wheel-breaking and Setting.
Cryptographic work on Tunny falls into two parts
(i) The recovery of wheel patterns or WHEEL-BREAKING
(ii) The recovery of message settings or SETTING.
The theoretical basis of wheel-breaking and setting is very similar, and for every method of setting there is a corresponding method of wheel-breaking which uses more traffic and more information.
Normal practice is therefore to select the most promising material enciphered on a given set of wheel patterns and to use this for wheel-breaking. When the wheel patterns are known, they can then be used for setting other messages enciphered on them.
It will be noticed that it is possible to determine
(i) relative but not absolute settings
(ii) wheel patterns of corresponding chis and psis (e.g. Χ4 Ψ4) only with the proviso that dots and crosses may be interchanged on both wheels. This does not apply if one of the wheels is involved in the limitation.
(c) Weaknesses of Tunny.
The fact that Tunny can be broken at all depends on the fact that P, Χ, Ψ', K and D have marked statistical, periodic or linguistic characteristics which distinguish them from random sequences of letters.
Back to General Report on Tunny. Contents.